Quantum computers are coming. And when they arrive, they are going to upend the way we protect sensitive data.
Unlike classical computers, quantum computers harness quantum mechanical effects — like superposition and entanglement — to process and store data in a form beyond the 0s and 1s that are digital bits. These “quantum bits” — or qubits — could open up massive computing power.

“Like many powerful technologies, you can use [quantum computing] for great good,” Rebecca Krauthamer, a technological ethicist and CEO of cybersecurity firm QuSecure, told Live Science. “And you can also use it for malicious purposes.”
When usable quantum computers first come online, most people — and even most large organizations — will still rely on classical computers. Cryptographers therefore need to come up with ways to protect data from powerful quantum computers, using programs that can run on a regular laptop.
That’s where the field of post-quantum cryptography comes in. Several groups of scientists are racing to develop cryptographic algorithms that can evade hacking by quantum computers before they are rolled out. Some of these cryptographic algorithms rely on newly developed equations, while others are turning to centuries-old ones. But all have one thing in common: They can’t be easily cracked by algorithms that run on a quantum computer.
“It’s like a foundation for a three-story building, and then we built a 100-story skyscraper on it.”
Michele Mosca, co-founder and CEO of cybersecurity company evolutionQ
The foundations of cryptography
Cryptography dates back thousands of years; the earliest known example is a cipher carved into ancient Egyptian stone in 1900 B.C. But the cryptography used by most software systems today relies on public key algorithms. In these systems, the computer uses algorithms — which often involve factoring the product of two large prime numbers — to generate both a public key and a private key. The public key is used to scramble the data, while the private key, which is available only to the sender, can be used to unscramble the data.
To crack such cryptography, hackers and other malefactors often must factor the products of very large prime numbers or try to find the private key by brute force — essentially throwing out guesses and seeing what sticks. This is a hard problem for classical computers because they have to test each guess one after another, which limits how quickly the factors can be identified.

A 100-story skyscraper on a three-story building
Nowadays, classical computers often stitch together multiple encryption algorithms, implemented at different locations, such as a hard disk or the internet.
“You can think of algorithms like building bricks,” Britta Hale, a computer scientist at the Naval Postgraduate School, told Live Science (Hale was speaking strictly in her capacity as an expert and not on behalf of the school or any organization.) When the bricks are stacked, each one makes up a small piece of the fortress that keeps out hackers.
But most of this cryptographic infrastructure was built on a foundation developed in the 1990s and early 2000s, when the internet was much less central to our lives and quantum computers were mainly thought experiments. “It’s like a foundation for a three-story building, and then we built a 100-story skyscraper on it,” Michele Mosca, co-founder and CEO of cybersecurity company evolutionQ, told Live Science. “And we’re kind of praying it’s OK.”
It might take a classical computer thousands or even billions of years to crack a really hard prime factorization algorithm, but a powerful quantum computer can often solve the same equation in a few hours. That’s because a quantum computer can run many calculations simultaneously by exploiting quantum superposition, in which qubits can exist in multiple states at once. In 1994, American mathematician Peter Shor showed that quantum computers can efficiently run algorithms that will quickly solve prime-number factoring problems. As a result, quantum computers could, in theory, tear down the cryptographic fortresses we currently use to protect our data.
Post-quantum cryptography aims to replace obsolete building blocks with less-hackable bricks, piece by piece. And the first step is to find the right math problems to use. In some cases, that means returning to equations that have been around for centuries.
Currently, the National Institute of Standards and Technology (NIST) is looking at four problems as potential foundations for post-quantum cryptography. Three belong to a mathematical family known as structured lattices. These problems ask questions about the vectors — mathematical terms that describe direction and magnitude between interconnected nodes — like the connection points in a spiderweb, Mosca said. These lattices can theoretically have an infinite number of nodes and exist in multiple dimensions.
Experts believe lattice problems will be hard for a quantum computer to crack because, unlike some other cryptographic algorithms, lattice problems don’t rely on factoring massive numbers.
Instead, they use the vectors between nodes to create a key and encrypt the data. Solving these problems may involve, for example, calculating the shortest vector in the lattice, or trying to determine which vectors are closest to one another. If you have the key — often a “good” starting vector — these problems may be relatively easy. But without that key, they are devilishly hard. That’s because no one has devised an algorithm, like Shor’s algorithm, that can efficiently solve these problems using quantum computing architecture.
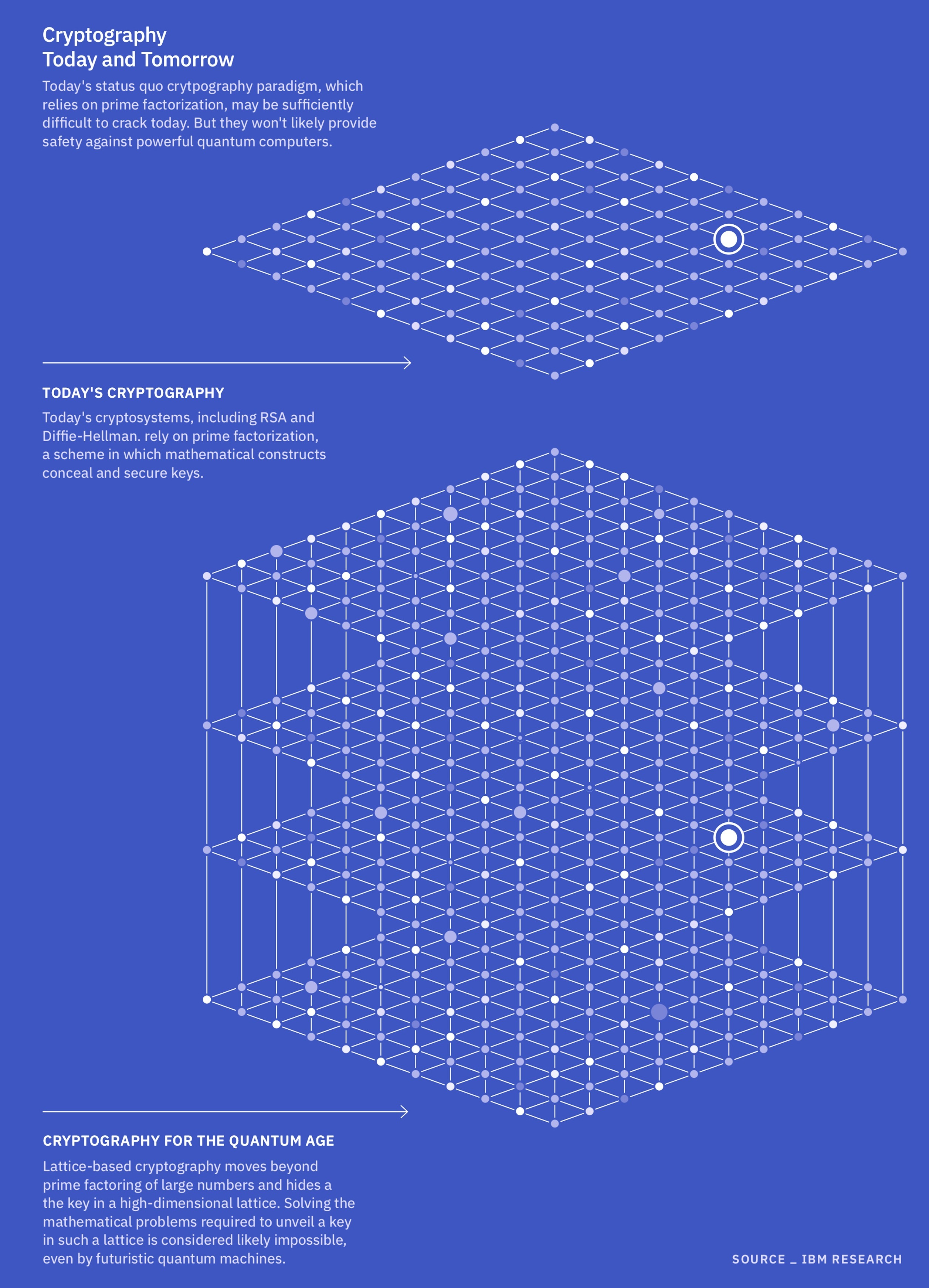
The fourth problem that NIST is considering belongs to a group called hash functions. Hash functions work by taking the virtual key for unlocking a specific point on a data table, scrambling that key and compressing it into a shorter code. This type of algorithm is already a cornerstone of modern cybersecurity, so in theory, it should be more straightforward to upgrade classical computers to a quantum-proof version compared with other post-quantum cryptographic schemes, Mosca said. And similarly to structured lattices, they can’t easily be solved by brute force alone; you need some clue as to what’s going on inside the “black box” key generator to figure them out within the age of the universe.
But these four problems don’t cover all of the potentially quantum-safe algorithms in existence. For example, the European Commission is looking at an error-correcting code known as the McEliece cryptosystem. Developed more than 40 years ago by American engineer Robert McEliece, this system uses random number generation to create a public and private key, as well as an encryption algorithm. The recipient of the private key uses a fixed cipher to decrypt the data.
McEliece encryption is largely considered both faster and more secure than the most commonly used public-key cryptosystem, called Rivest-Shamir-Adleman. As with a hash function, would-be hackers need some insight into its black-box encryption to solve it. On the plus side, experts consider this system very safe; on the downside, even the keys to unscramble the data must be processed using extremely large, cumbersome matrices, requiring a lot of energy to run.
A similar error-correcting code, known as Hamming Quasi-Cyclic (HQC), was recently selected by NIST as a backup to its primary candidates. Its primary advantage over the classic McEliece system is that it utilizes smaller key and ciphertext sizes.
Another type of algorithm that sometimes comes up in conversations about post-quantum cryptography is the elliptic curve, Bharat Rawal, a computer and data scientist at Capitol Technology University in Maryland, told Live Science. These problems go back at least to ancient Greece. Elliptic curve cryptography exploits basic algebra — calculating the points on a curved line — to encrypt keys. Some experts believe a new elliptic curve algorithm could evade hacking by a quantum computer. However, others argue that a hacker could hypothetically use Shor’s algorithm on a quantum computer to break most known elliptic curve algorithms, making them a less-secure option.
No silver bullet
In the race to find quantum-safe cryptographic equations, there won’t be a silver bullet or a one-size-fits-all solution. For example, there’s always a trade-off in processing power; it wouldn’t make much sense to use complex, power-hungry algorithms to secure low-priority data when a simpler system might be perfectly adequate.
“It’s not like one algorithm [combination] will be the way to go; it depends on what they’re protecting,” Hale said.
In fact, it’s valuable for organizations that use classical computers to have more than one algorithm that can protect their data from quantum threats. That way, “if one is proven to be vulnerable, you can easily switch to one that was not proven vulnerable,” Krauthamer said. Krauthamer’s team is currently working with the U.S. Army to improve the organization’s ability to seamlessly switch between quantum-safe algorithms — a feature known as cryptographic agility.
Even though useful (or “cryptographically relevant”) quantum computers are still several years away, it is vital to start preparing for them now, experts said. “It can take many years to upgrade existing systems to be ready for post-quantum cryptography,” Douglas Van Bossuyt, a systems engineer at the Naval Postgraduate School, told Live Science in an email. (Van Bossuyt was speaking strictly as a subject-matter expert and not on behalf of the Naval Postgraduate School, the Navy or the Department of Defense.) Some systems are tough to upgrade from a coding standpoint. And some, such as those aboard military craft, can be difficult — or even impossible — for scientists and engineers to access physically.
Other experts agree that post-quantum cryptography is a pressing issue. “There’s also the chance that, again, because quantum computers are so powerful, we won’t actually know when an organization gets access to such a powerful machine,” Krauthamer said.
There’s also the threat of “harvest-now, decrypt-later” attacks. Malicious actors can scoop up sensitive encrypted data and save it until they have access to a quantum computer that’s capable of cracking the encryption. These types of attacks can have a wide range of targets, including bank accounts, personal health information and national security databases. The sooner we can protect such data from quantum computers, the better, Van Bossuyt said.
And as with any cybersecurity approach, post-quantum cryptography won’t represent an end point. The arms race between hackers and security professionals will continue to evolve well into the future, in ways that we can only begin to predict. It may mean developing encryption algorithms that run on a quantum computer as opposed to a classical one or finding ways to thwart quantum artificial intelligence, Rawal said.
“The world needs to keep working on this because if these [post-quantum equations] are broken, we don’t want to wait 20 years to come up with the replacement,” Mosca said.


