Are OTPs The Real Problem, Or Is It The 32,543 Unique Passwords We’re Supposed To Have?
MFA is a nice addition to security. It adds another layer on top of the username and password combo which has become the standard for logins, and makes it more difficult for someone who guesses your password to gain access to your accounts. The SMS one time passwords are popular for many services, but unfortunately they are sadly easy to steal. An attacker can intercept the OTP text to your phone, or set up a webpage that looks official and which will query your authentic service provider to confirm username and password, grab the OTP sent to your phone and gain access to your accounts that way.
Replacing OTP with either a physical token, be it a USB stick or your smartphone for MFA, is a step up. Alternatively biometrics or a local PIN can also work because in both these cases the MFA traffic can be encrypted. That means even if you are logging into a nefarious site or have someone monitoring your traffic it becomes much more difficult to steal your account. There are still ways of grabbing session cookies and other tokens used to authenticate you, but it requires far more technical know how than intercepting a OTP over SMS.
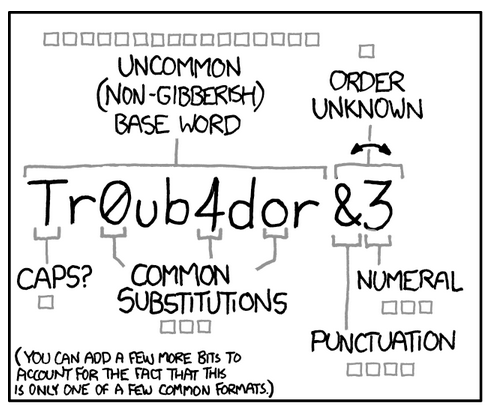
Unfortunately this does not address the root cause of all of this. The real problem is the theoretically unique password tied to your user. With every single website, credit card, service and account you are asked to create and recall a unique password. This is not a reasonable expectation for your average ape descendant, we will cheat by reusing passwords, making them in predictable patterns or even writing them down. This is exacerbated by the random rules associated with your password. some allow space as a character while others do not, nor do humans use numbers in the way that password fields expect.
The processing power of modern consumer GPUs can blast through simple passwords in no time, but our brains are not wired to remember dozens of 15+ character strings. The training that most people have had doesn’t help either, as replacing an e with a 3 or l with a 1 doesn’t really add extra protection and will likely make the password harder to recall; was it Pas5word or Pa5sword or Pas5w0rd or … ? This is why Have I Been Pwned currently has a list of 17,295,033,626 compromised accounts.
If sites would at least all agree to accept the space character things could get a little better. A short sentence with proper capitalization and punctuation makes for a password easier to remember than a random series of characters and much harder for a computer to guess. There are also various password managers you can use which will generate passwords for you and keep track of them. You do have to trust they will never be compromised themselves, and that no one guesses the password you used for that account. It is also a password you really can’t afford to lose, which means it will get written down somewhere.
Until the industry can come up with a reasonable alternative to the classic username and password pairing, adding extra steps will annoy many users and really is only another layer of duct tape on a problem that needs a proper fix. For many, if the password for their account isn’t ready in autofill then their password is the ‘I forgot my password link’.
If even you don’t know your password it’s sort of secure, right?